What is (Wireless / Computer) Networking?
In the world of computers, networking is the practice of linking two or more computing devices together for the purpose of sharing data. Networks are built with a mix of computer hardware and computer software.
Area Networks:
Networks can be categorized in several different ways. One approach defines the type of network according to the geographic area it spans. Local area networks (LANs), for example, typically reach across a single home, whereas wide area networks (WANs), reach across cities, states, or even across the world. The Internet is the world's largest public WAN.
Network Design:
Computer networks also differ in their design. The two types of high-level network design are called client-server and peer-to-peer. Client-server networks feature centralized server computers that store email, Web pages, files and or applications. On a peer-to-peer network, conversely, all computers tend to support the same functions. Client-server networks are much more common in business and peer-to-peer networks much more common in homes.
A network topology represents its layout or structure from the point of view of data flow. In so-called bus networks, for example, all of the computers share and communicate across one common conduit, whereas in a star network, all data flows through one centralized device. Common types of network topologies include bus, star, ring and mesh.
Network Protocols:
In networking, the communication language used by computer devices is called the protocol. Yet another way to classify computer networks is by the set of protocols they support. Networks often implement multiple protocols to support specific applications. Popular protocols include TCP/IP, the most common protocol found on the Internet and in home networks.
Wired vs Wireless Networking:
Many of the same network protocols, like TCP/IP, work in both wired and wireless networks. Networks with Ethernet cables predominated in businesses, schools, and homes for several decades. Recently, however, wireless networking alternatives have emerged as the premier technology for building new computer networks.
Fundamental Computer Networks Concepts

In the world of computers, networking is the practice of linking two or more computing devices together for the purpose of sharing data. Networks are built with a combination of computer hardware and computer software. Some explanations of networking found in books and tutorials are highly technical, designed for students and professionals, while others are geared more to home and business uses of computer networks.
Introduction to Peer to Peer Networks
Peer to peer is an approach to computer networking where all computers share equivalent responsibility for processing data. Peer-to-peer networking (also known simply as peer networking) differs from client-server networking, where certain devices have responsibility for providing or "serving" data and other devices consume or otherwise act as "clients" of those servers.
Characteristics of a Peer Network:
Peer to peer networking is common on small local area networks (LANs), particularly home networks. Both wired and wireless home networks can be configured as peer to peer environments.
Computers in a peer to peer network run the same networking protocols and software. Peer networks are also often situated physically near to each other, typically in homes, small businesses or schools. Some peer networks, however, utilize the Internet and are geographically dispersed worldwide.
Home networks that utilize broadband routers are hybrid peer to peer and client-server environments. The router provides centralized Internet connection sharing, but file, printer and other resource sharing is managed directly between the local computers involved.
Peer to Peer and P2P Networks:
Internet-based peer to peer networks emerged in the 1990s due to the development of P2P file sharing networks like Napster. Technically, many P2P networks (including the original Napster) are not pure peer networks but rather hybrid designs as they utilize central servers for some functions such as search.
Peer to Peer and Ad Hoc Wi-Fi Networks
Wi-Fi wireless networks support so-called ad hoc connections between devices. Ad hoc Wi-Fi networks are pure peer to peer compared to those utilizing wireless routers as an intermediate device.
Benefits of a Peer to Peer Network:
You can configure computers in peer to peer workgroups to allow sharing of files, printers and other resources across all of the devices. Peer networks allow data to be shared easily in both directions, whether for downloads to your computer or uploads from your computer.
On the Internet, peer to peer networks handle a very high volume of file sharing traffic by distributing the load across many computers. Because they do not rely exclusively on central servers, P2P networks both scale better and are more resilient than client-server networks in case of failures or traffic bottlenecks.
What is Wireless Computer Networking?
Wireless networks utilize radio waves and/or microwaves to maintain communication channels between computers. Wireless networking is a more modern alternative to wired networking that relies on copper and/or fiber optic cabling between network devices.
A wireless network offers advantages and disadvantages compared to a wired network. Advantages of wireless include mobility and elimination of unsightly cables. Disadvantages of wireless include the potential for radio interference due to weather, other wireless devices, or obstructions like walls.
Wireless is rapidly gaining in popularity for both home and business networking. Wireless technology continues to improve, and the cost of wireless products continues to decrease. Popular wireless local area networking (WLAN) products conform to the 802.11 "Wi-Fi" standards. The gear a person needs to build wireless networks includes network adapters (NICs), access points (APs), and routers.
What Is a Computer Operating System?
Computers use low-level software called an operating system (O/S) to help people build and run their own programs. Operating system software runs not just on laptop computers but also on cell phones, network routers and other so-called embedded devices.
Types of Operating Systems
The best-known operating systems are those used on personal computers:
* Microsoft Windows
* Mac OS X
* Linux
Some operating systems are designed for certain types of equipment, such as
* Google Android (a variant of Linux), and Symbian - for cell phones
* Solaris, HP-UX, DG-UX, and other variants of Unix - for server computers
* DEC VMS (Virtual Memory System) - for mainframe computers
Other operating systems enjoyed a period of notoriety but are of only historical interest now:
* Novell Netware was a popular O/S for PCs in the 1990s
* IBM OS/2 was an early PC O/S that competed with Microsoft Windows for a time but had limited success
* Multics was an especially innovative operating system created in the 1960s for mainframes, that influenced the later development of Unix
Network Operating Systems:
A modern O/S contains much built-in software designed to simplify networking of a computer. Typical O/S software includes an implementation of TCP/IP protocol stack and related utility programs like ping and traceroute. This includes the necessary device drivers and other software to automatically enable a device's Ethernet interface. Mobile devices also normally provide the programs needed to enable Wi-Fi, Bluetooth, or other wireless connectivity.
The early versions of Microsoft Windows did not provide any computer networking support. Microsoft added basic networking capability into its operating system starting with Windows 95 and Windows for Workgroups. Microsoft also introduced its Internet Connection Sharing (ICS) feature in Windows 98 Second Edition (Win98 SE). Contrast that with Unix, which was designed from the beginning with networking in view. Nearly any consumer O/S today qualifies as a network operating system due to the popularity of the Internet.
Embedded Operating Systems:
A so-called embedded system supports no or limited configuration of its software. Embedded systems like routers, for example, typically include a pre-configured Web server, DHCP server, and some utilities but do not allow the installation of new programs. Examples of embedded operating systems for routers include:
* Cisco IOS (Internetwork Operating System)
* DD-WRT
* Juniper Junos
An embedded OS can also be found inside an increasing number of consumer gadgets including phones (iPhone OS), PDAs (Windows CE), and digital media players (ipodlinux).
What Is Keylogger ?
Definition: A keylogger is a hardware device or a software program that records the real time activity of a computer user including the keyboard keys they press.
Keyloggers are used in IT organizations to troubleshoot technical problems with computers and business networks. Keyloggers can also be used by a family (or business) to monitor the network usage of people without their direct knowledge. Finally, malicious individuals may use keyloggers on public computers to steal passwords or credit card information.
Keylogger software is freely available on the Internet. These keyloggers allow not only keyboard keystrokes to be captured but also are often capable of collecting screen captures from the computer. Normal keylogging programs store their data on the local hard drive, but some are programmed to automatically transmit data over the network to a remote computer or Web server.
Detecting the presence of a keylogger on a computer can be difficult. So-called anti-keylogging programs have been developed to thwart keylogging systems, and these are often effective when used properly.
What Is Computer Port ?
Definition: In computer networking, the term port can refer to either physical or virtual connection points.
Physical network ports allow connecting cables to computers, routers, modems and other peripheral devices. Several different types of physical ports available on computer network hardware include:
* Ethernet ports--Ethernet is a physical and data link layer technology for local area networks (LANs). Ethernet was invented by engineer Robert Metcalfe.
When first widely deployed in the 1980s, Ethernet supported a maximum theoretical data rate of 10 megabits per second (Mbps). Later, so-called "Fast Ethernet" standards increased this maximum data rate to 100 Mbps. Today, Gigabit Ethernet technology further extends peak performance up to 1000 Mbps.
Higher level network protocols like Internet Protocol (IP) use Ethernet as their transmission medium. Data travels over Ethernet inside protocol units called frames.
The run length of individual Ethernet cables is limited to roughly 100 meters, but Ethernet networks can be easily extended to link entire schools or office buildings using network bridge devices.
* USB ports--A USB port is a standard cable connection interface on personal computers and consumer electronics. USB ports allow stand-alone electronic devices to be connected via cables to a computer (or to each other).
USB stands for Universal Serial Bus, an industry standard for short-distance digital data communications. USB allows data to be transferred between devices. USB ports can also supply electric power across the cable to devices without their own power source.
Both wired and wireless versions of the USB standard exist, although only the wired version involves USB ports and cables.
What Can You Plug Into a USB Port?:
Many types of consumer electronics support USB interfaces. These types of equipment are most commonly used for computer networking:
* USB network adapters
* USB broadband and cellular modems for Internet access
* USB printers to be shared on a home network
For computer-to-computer file transfers without a network, USB keys are also sometimes used to copy files between devices.
Multiple USB devices can also be connected to each other using a USB hub. A USB hub plugs into one USB port and contains additional ports for other devices to connect subsequently.
Usage Model:
Connect two devices directly with one USB cable by plugging each end into a USB port. If using a USB hub, plug a separate cable into each device and connect them to the hub individually.
You may plug cables into a USB port at any time regardless of whether the devices involved are powered on or off. However, do not remove cables from a USB port arbitrarily, as this can lose or corrupt data. Follow instructions provided with your equipment before unplugging USB cables.
Many PCs feature more than one USB port, but do not plug both ends of a cable into the same device, as this can cause electrical damage.
USB-B and Other Types of Ports:
A few different types of physical layouts exist for USB ports. The standard layout for computers, called USB-B, is a rectangular connection point approximately 1.4 cm (9/16 in) length by 0.65 cm (1/4 in) height.
Printers and some other devices may use smaller types of USB ports including a standard called USB-A. To connect a device having USB-B ports to a device with another type, simply use the correct type of cable with appropriate interfaces on each end.
Versions of USB:
The USB industry standard exists in multiple versions including 1.1, 2.0 and 3.0. However, USB ports feature identical physical layouts no matter the version of USB supported.
Alternative Technologies:
USB ports are an alternative to the serial and parallel ports available on older PCs. USB ports support much faster (often 100x or greater) data transfers than serial or parallel.
For computer networking, Ethernet ports are sometimes used instead of USB. For some types of computer peripherals, FIreWire ports are also sometimes available. Both Ethernet and FireWire can offer faster performance than USB, although these interfaces do not supply any power across the wire.
* serial ports--In computer networking, a serial port enables external modems to connect to a PC or network router via a serial cable. The term "serial" signifies that data sent in one direction always travels over a single wire within the cable.
The prevailing standard for traditional serial port communications historically has been RS-232. These serial ports and cables are the same used for PC keyboards and other computer peripheral devices (see sidebar). Serial ports and cables for RS-232 PCs generally feature 9-pin DE-9 connectors, although 25-pin DB-25 and other variations exist on specialized hardware. The alternative RS-422 standard applies on many Macintosh computers.
Both of these standards are gradually becoming obsolete in favor of USB or FireWire standard ports and serial communication.
Virtual ports are part of TCP/IP networking. These ports allow software applications to share hardware resources without interfering with each other. Computers and routers automatically manage network traffic traveling via their virtual ports. Network firewalls additionally provide some control over the flow of traffic on each virtual port for security purposes.
Introduction to Client Server Networks
The term client-server refers to a popular model for computer networking that utilizes client and server devices each designed for specific purposes. The client-server model can be used on the Internet as well as local area networks (LANs). Examples of client-server systems on the Internet include Web browsers and Web servers, FTP clients and servers, and DNS.
Client and Server Devices:
Client/server networking grew in popularity many years ago as personal computers (PCs) became the common alternative to older mainframe computers. Client devices are typically PCs with network software applications installed that request and receive information over the network. Mobile devices as well as desktop computers can both function as clients.
A server device typically stores files and databases including more complex applications like Web sites. Server devices often feature higher-powered central processors, more memory, and larger disk drives than clients.
Client-Server Applications:
The client-server model distinguishes between applications as well as devices. Network clients make requests to a server by sending messages, and servers respond to their clients by acting on each request and returning results. One server generally supports numerous clients, and multiple servers can be networked together in a pool to handle the increased processing load as the number of clients grows.
A client computer and a server computer are usually two separate devices, each customized for their designed purpose. For example, a Web client works best with a large screen display, while a Web server does not need any display at all and can be located anywhere in the world. However, in some cases a given device can function both as a client and a server for the same application. Likewise, a device that is a server for one application can simultaneously act as a client to other servers, for different applications.
[Some of the most popular applications on the Internet follow the client-server model including email, FTP and Web services. Each of these clients features a user interface (either graphic- or text-based) and a client application that allows the user to connect to servers. In the case of email and FTP, users enter a computer name (or sometimes an IP address) into the interface to set up connections to the server.
Local Client-Server Networks
Many home networks utilize client-server systems without even realizing it. Broadband routers, for example, contain DHCP servers that provide IP addresses to the home computers (DHCP clients). Other types of network servers found in home include print servers and backup servers.
Client-Server vs Peer-to-Peer and Other Models:
The client-server model was originally developed to allow more users to share access to database applications. Compared to the mainframe approach, client-server offers improved scalability because connections can be made as needed rather than being fixed. The client-server model also supports modular applications that can make the job of creating software easier. In so-called "two-tier" and "three-tier" types of client-server systems, software applications are separated into modular pieces, and each piece is installed on clients or servers specialized for that subsystem.
Client-server is just one approach to managing network applications The primary alternative, peer-to-peer networking, models all devices as having equivalent capability rather than specialized client or server roles. Compared to client-server, peer to peer networks offer some advantages such as more flexibility in growing the system to handle large number of clients. Client-server networks generally offer advantages in keeping data secure.
OSI Model Reference Guide
The Open Systems Interconnection (OSI) reference model has been an essential element of computer network design since its ratification in 1984. The OSI is an abstract model of how network protocols and equipment should communicate and work together (interoperate).
The OSI model is a technology standard maintained by the International Standards Organization (ISO). Although today's technologies do not fully conform to the standard, it remains a useful introduction to the study of network architecture.


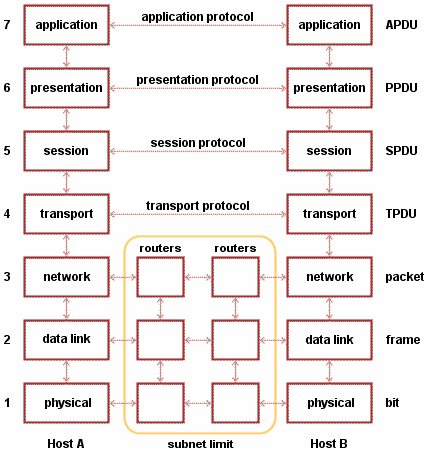

The OSI Model Stack:
The OSI model divides the complex task of computer-to-computer communications, traditionally called internetworking, into a series of stages known as layers. Layers in the OSI model are ordered from lowest level to highest. Together, these layers comprise the OSI stack. The stack contains seven layers in two groups:
Upper layers -
7. application
6. presentation
5. session
Lower layers -
4. transport
3. network
2. data link
1. physical
Upper Layers of the OSI Model:
OSI designates the application, presentation, and session stages of the stack as the upper layers. Generally speaking, software in these layers performs application-specific functions like data formatting, encryption, and connection management.
Examples of upper layer technologies in the OSI model are HTTP, SSL and NFS.
Lower Layers of the OSI Model:
The remaining lower layers of the OSI model provide more primitive network-specific functions like routing, addressing, and flow control. Examples of lower layer technologies in the OSI model are TCP, IP, and Ethernet.
Benefits of the OSI Model:
By separating the network communications into logical smaller pieces, the OSI model simplifies how network protocols are designed. The OSI model was designed to ensure different types of equipment (such as network adapters, hubs, and routers) would all be compatible even if built by different manufacturers. A product from one network equipment vendor that implements OSI Layer 2 functionality, for example, will be much more likely to interoperate with another vendor's OSI Layer 3 product because both vendors are following the same model.
The OSI model also makes network designs more extensible as new protocols and other network services are generally easier to add to a layered architecture than to a monolithic one.
Network Topologies
In computer networking, topology refers to the layout of connected devices. This article introduces the standard topologies of networking.
Topology in Network Design:
Think of a topology as a network's virtual shape or structure. This shape does not necessarily correspond to the actual physical layout of the devices on the network. For example, the computers on a home LAN may be arranged in a circle in a family room, but it would be highly unlikely to find a ring topology there.
Network topologies are categorized into the following basic types:
* bus
* ring
* star
* tree
* mesh
Bus Topology:
Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. A single cable, the backbone functions as a shared communication medium that devices attach or tap into with an interface connector. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message.
Ethernet bus topologies are relatively easy to install and don't require much cabling compared to the alternatives. 10Base-2 ("ThinNet") and 10Base-5 ("ThickNet") both were popular Ethernet cabling options many years ago for bus topologies. However, bus networks work best with a limited number of devices. If more than a few dozen computers are added to a network bus, performance problems will likely result. In addition, if the backbone cable fails, the entire network effectively becomes unusable.
Ring Topology:
In a ring network, every device has exactly two neighbors for communication purposes. All messages travel through a ring in the same direction (either "clockwise" or "counterclockwise"). A failure in any cable or device breaks the loop and can take down the entire network.
To implement a ring network, one typically uses FDDI, SONET, or Token Ring technology. Ring topologies are found in some office buildings or school campuses.
Star Topology:
Many home networks use the star topology. A star network features a central connection point called a "hub" that may be a hub, switch or router. Devices typically connect to the hub with Unshielded Twisted Pair (UTP) Ethernet.
Compared to the bus topology, a star network generally requires more cable, but a failure in any star network cable will only take down one computer's network access and not the entire LAN. (If the hub fails, however, the entire network also fails.)
Tree Topology:
Tree topologies integrate multiple star topologies together onto a bus. In its simplest form, only hub devices connect directly to the tree bus, and each hub functions as the "root" of a tree of devices. This bus/star hybrid approach supports future expandability of the network much better than a bus (limited in the number of devices due to the broadcast traffic it generates) or a star (limited by the number of hub connection points) alone.

Mesh Topology:
Mesh topologies involve the concept of routes. Unlike each of the previous topologies, messages sent on a mesh network can take any of several possible paths from source to destination. (Recall that even in a ring, although two cable paths exist, messages can only travel in one direction.) Some WANs, most notably the Internet, employ mesh routing.
A mesh network in which every device connects to every other is called a full mesh. As shown in the illustration below, partial mesh networks also exist in which some devices connect only indirectly to others.
Summary:
Topologies remain an important part of network design theory. You can probably build a home or small business computer network without understanding the difference between a bus design and a star design, but becoming familiar with the standard topologies gives you a better understanding of important networking concepts like hubs, broadcasts, and routes.
What Is Packet Switching on Computer Networks?
Packet switching is the approach used by some computer network protocols to deliver data across a local or long distance connection. Examples of packet switching protocols are Frame Relay, IP and X.25.
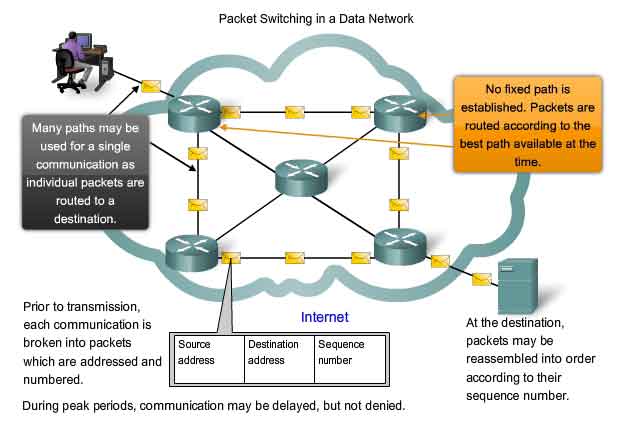
How Packet Switching Works:
Packet switching entails packaging data in specially formatted units (called packets) that are typically routed from source to destination using network switches and routers. Each packet contains address information that identifies the sending computer and intended recipient. Using these addresses, network switches and routers determine how best to transfer the packet between hops on the path to its destination.
Pros and Cons of Packet Switching:

Packet switching is the alternative to circuit switching protocols used historically for telephone (voice) networks and sometimes with ISDN connections.
Compared to circuit switching, packet switching offers the following:
* More efficient use of overall network bandwidth due to flexibility in routing the smaller packets over shared links. Packet switching networks are often cheaper to build as less equipment is needed given this ability to share.
* Longer delays in receiving messages due to the time required to package and route packets. For many applications, delays are not long enough to be significant, but for high-performance applications like real-time video, additional data compression and QoS technology is often required to achieve the required performance levels.
* Potential for network security risks due to the use of shared physical links. Protocols and other related elements on packet switching networks must designed with the appropriate security precautions.
Computer Architecture Basics
Understanding these fundamental concepts in computer architecture is essential to learning computer networking.
Working with Binary and Hexadecimal Numbers:
Network addresses, network masks, and encryption keys all typically utilize binary and hexadecimal numbers. Learning binary and hexadecimal numbering concepts will improve your ability to set up and manage computer networks.
Binary-Decimal Number Conversion Calculator:
This interactive form computes binary-to-decimal and decimal-to-binary conversions. Unlike ordinary calculators, this calculator displays step-by-step logic as a helpful teaching aid.
Bits:
Bits are the smallest unit of data transfer in computer networking. Bits represent binary values like "on / off," "yes / no," and "true / false."
Bytes:
A byte is a sequence of bits. In computer networking, some network protocols send and receive data in the form of byte sequences. These are called byte-oriented protocols.
What Is the Difference Between Bits and Bytes?
Both "bits" and "bytes" refer to digital data transmitted over a network connection. Both can hold network addresses or port numbers, for example. This page describes the difference between bits and bytes.
Kilobits - Megabits - Gigabits:
A kilobit in computer networking represents 1000 bits of data. Much larger amounts of data can also be represented in units of megabits or gigabits. Kilobits, megabits and gigabits traveling over a computer network are typically measured per second.
Addresses:
Network addresses uniquely identify the network interface of a computer or similar device. Network addressing differs from memory and other types of addressing in computer architecture.
(Computer) Ports:
In computer networking, a port represents a communication channel or endpoint. Computer ports can refer to either physical or virtual connections.
Network Programming - Windows, Unix and Socket
Did you know that network programming is the use of software APIs and development tools to build network-aware applications? Windows, Mac and Unix/Linux network programs all share some of the same fundamental concepts including sockets. So-called cross-platform network programming environments like Java and Python also exist.
1. Networking with Python
What Is a Socket?
A socket is a software construction representing a single connection between two network applications. Network programmers typically use socket libraries like Berkeley Sockets or Winsock rather than coding directly to lower level socket APIs.
API - Application Programming Interface
Application Programming Interfaces (APIs) provide controlled access to software libraries and modules. Networking APIs like WinSock are entry points to libraries that implement network communication protocols.
Introduction to Socket Programming
Sockets allow application software to communicate over networks using standard mechanisms built into hardware and operating systems.
Ports and Port Numbers
A port number represents an endpoint or "channel" for network communications. Port numbers allow different applications on the same computer to utilize network resources without interfering with each other.
WinSock
WinSock is the standard sockets programming API for the Windows operating system.
RPC - Remote Procedure Call
RPC is a network programming model for point-to-point communication within or between software applications. In RPC, the sender makes a request in the form of a procedure, function, or method call.
XML-RPC
XML-RPC is a network programming technique that uses XML to make procedure calls to software running on remote devices.

"Programming Python"
The ultimate book for all but the most experienced Python developers; "Programming Python" teaches the principles of rapid application development through scripting using the Python programming language.
"Jython - Python Programming with the Java Class Libraries"
Improve your productivity by learning how to utilize Python programming within the Java environment. The Python language implementation known as Jython makes it all possible.